6 Important IT Policies Any Size Company Should Implement
Many small businesses make the mistake of skipping policies. They feel that things don’t need to be so formal. They’ll just tell staff what’s expected when it comes up and think that’s good enough.
But this way of thinking can cause issues for small and mid-sized business owners. Employees aren’t mind readers. Things that you think are obvious, might not be to them.
Not having policies can also leave you in poor legal standing should a problem occur. Such as a lawsuit due to misuse of a company device or email account.
Did you know that 77% of employees access their social media accounts while at work? Further, 19% of them average 1 full working hour a day spent on social media. In some cases, employees are ignoring a company policy. But in others, there is no specific policy for them to follow.
IT policies are an important part of your IT security and technology management. So, no matter what size your business is, you should have them. We’ll get you started with some of the most important IT policies your company should have in place.
Do You Have These IT Policies? (If Not, You Should)
Password Security Policy
About 77% of all cloud data breaches originate from compromised passwords. Compromised credentials are also now the number one cause of data breaches globally.
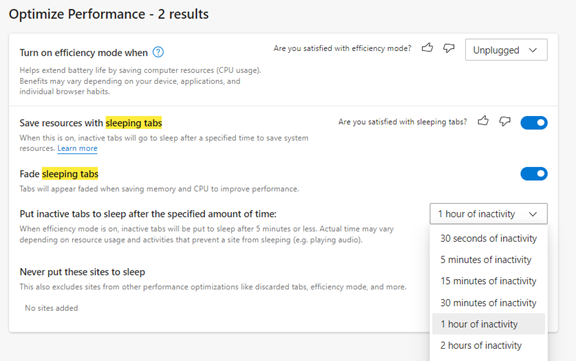
A password security policy will lay out for your team how to handle their login passwords. It should include things like:
- How long passwords should be
- How to construct passwords (e.g., using at least one number and symbol)
- Where and how to store passwords
- The use of multi-factor authentication (if it’s required)
- How often to change passwords
Acceptable Use Policy (AUP)
The Acceptable Use Policy is an overarching policy. It includes how to properly use technology and data in your organization. This policy will govern things like device security. For example, you may need employees to keep devices updated. If this is the case, You should include that in this policy.
Another thing to include in your AUP would be where it is acceptable to use company devices. You may also restrict remote employees from sharing work devices with family members.
Data is another area of the AUP. It should dictate how to store and handle data. The policy might require an encrypted environment for security.
Cloud & App Use Policy
The use of unauthorized cloud applications by employees has become a big problem. It’s estimated that the use of this “shadow IT” ranges from 30% to 60% of a company’s cloud use.
Often, employees use cloud apps on their own because they don’t know any better. They don’t realize that using unapproved cloud tools for company data is a major security risk.
A cloud and app use policy will tell employees what cloud and mobile apps are okay to use for business data. It should restrict the use of unapproved applications. It should also provide a way to suggest apps that would enhance productivity.
Bring Your Own Device (BYOD) Policy
Approximately 83% of companies use a BYOD approach for employee mobile use. Allowing employees to use their own smartphones for work saves companies money. It can also be more convenient for employees because they don’t need to carry around a second device.
But if you don’t have a policy that dictates the use of BYOD, there can be security and other issues. Employee devices may be vulnerable to attack if the operating system isn’t updated. There can also be confusion about compensation for the use of personal devices at work.
The BYOD policy clarifies the use of employee devices for business. Including the required security of those devices. It may also note the required installation of an endpoint management app. It should also cover compensation for business use of personal devices.
Wi-Fi Use Policy
Public Wi-Fi is an issue when it comes to cybersecurity. 61% of surveyed companies say employees connect to public Wi-Fi from company-owned devices.
Many employees won’t think twice about logging in to a company app or email account. Even when on a public internet connection. This could expose those credentials and lead to a breach of your company network.
Your Wi-Fi use policy will explain how employees are to ensure they have safe connections. It may dictate the use of a company VPN. Your policy may also restrict the activities employees can do when on public Wi-Fi. Such as not entering passwords or payment card details into a form.
Social Media Use Policy
With social media use at work so common, it’s important to address it. Otherwise, endless scrolling and posting could steal hours of productivity every week.
Include details in your social media policy, such as:
- Restricting when employees can access personal social media
- Restricting what employees can post about the company
- Noting “safe selfie zones” or facility areas that are not okay for public images
Get Help Improving Your IT Policy Documentation & Security
We can help your organization address IT policy deficiencies and security issues. Reach out today to schedule a consultation to get started.
This Article has been Republished with Permission from The Technology Press.